Cybercriminals linked to China are operating with increasing intensity, with their main targets being governments and the transportation industry, according to a report published by ESET Research. The report summarizes the activity of Advanced Persistent Threat (APT) groups from April to September 2024.
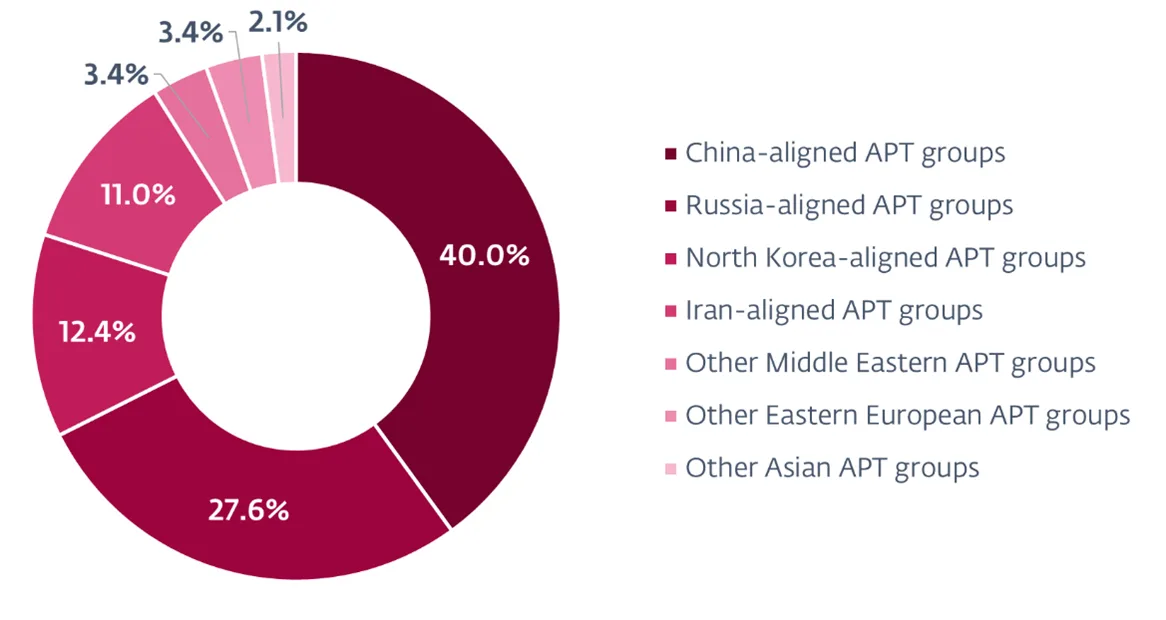
Groups tied to China can be attributed to as many as 40 percent of the APT attacks that took place in Q2 and Q3 2024. This makes them the largest group of cybercriminals involved in advanced actions of this type. Their activity has almost doubled compared to the previous half-year.
“The scale of operation of cybercriminals in APT groups is tremendous. They plan their attacks, focusing particularly on government entities, the defense sector, and strategic industries. Economic and political espionage, as well as spreading disinformation and panic, are one of their main objectives,” says Beniamin Szczepankiewicz, an analyst at the ESET antivirus laboratory.
In the second and third quarters of 2024, ESET Research observed a significant intensification of attacks conducted by the China-linked MirrorFace group. Usually focusing on Japanese entities, it has for the first time also targeted an EU diplomatic organization. An upcoming World Expo event to be held in Osaka, Japan in 2025 was used as bait. The email message contained a link to a ZIP archive, which in turn contained a file posing as a Word document, which was in fact used to install malware on the victims’ computers.
The MirrorFace group also continued a campaign affecting the transportation industry, which it began at the beginning of 2024. It is aimed at targets not only in Europe but also in the Middle East and Asia. The operation procedure remains the same in almost every case: the group uses malicious software called Korplug, which is mainly installed through removable media. Other techniques used by China-linked cybercriminals to gain access to victims’ systems include exploiting vulnerabilities in publicly available internet applications and spearphishing (highly sophisticated social engineering methods of manipulation and information extraction from specific people).
The APT attack sources for Q2-Q3 2024 sheds light on the intensifying activity of cybercriminals, as governments, the transportation industry, and – for the first time – EU diplomacy are being targeted by Chinese hackers.
Source: https://managerplus.pl/rosnie-aktywnosc-chinskich-cyberprzestepcow-na-celowniku-rzady-branza-transportowa-i-po-raz-pierwszy-dyplomacja-ue-45594