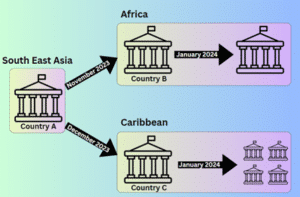
- Sharp Dragon, a Chinese group previously known as Sharp Panda, is conducting a spying campaign in Africa and the Caribbean.
- The campaign has so far used Cobalt Strike Beacon payloads, allowing the creation of a backdoor in public administration systems.
- Sharp Dragon’s strategic expansion towards Africa and the Caribbean signifies broader efforts by Chinese cyber entities to increase their presence and influence in these regions. The evolving tactics of Sharp Dragon highlight the dynamic nature of cyber threats, especially towards regions that have been historically overlooked.
A Chinese cyber-espionage campaign is currently targeting government organizations in Africa and the Caribbean, according to experts from Check Point Research who are investigating the matter. The responsibility is attributed to the group Sharp Dragon (formerly Sharp Panda), which has reportedly used Cobalt Strike Beacon payloads to create a backdoor.
Since 2021, cybersecurity analysts at Check Point Research have been closely monitoring the activities of Sharp Dragon, a Chinese group previously known as Sharp Panda. Their tactics have primarily included highly targeted phishing emails resulting in the deployment of malware such as VictoryDLL or the Soul framework.
However, in recent months, there has been a noticeable shift. The Sharp Dragon group has redirected its attention to government organizations in Africa and the Caribbean. These actions are consistent with Sharp Dragon’s established modus operandi, which involves compromising prestigious email accounts to disseminate phishing documents using a remote template armed with RoyalRoad. Unlike previous methods, the baits now use Cobalt Strike Beacon, indicating a strategic adaptation aimed at enhancing their infiltration capabilities.
Figure 1: Sharp Dragon’s campaign focuses on Africa and the Caribbean
Chinese cybercriminals are using highly personalized phishing emails, often impersonating official correspondence, to entice victims to open malicious attachments or click on malicious links. These attachments or links install payloads that have evolved from custom malware like VictoryDLL and the Soul framework to more widely used tools such as Cobalt Strike Beacon. Upon successful deployment, the malware establishes a foothold in the victim’s system, enabling threat actors to conduct reconnaissance and gather information about the target environment. This reconnaissance phase allows Sharp Dragon to identify high-value targets and tailor their attack strategy accordingly.
Figure 2: Example of an infection chain
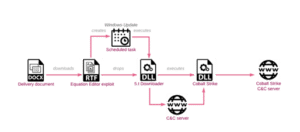
Such an infection chain underscores Sharp Dragon’s sophisticated approach to cyber operations, emphasizing meticulous planning, reconnaissance, and exploitation of security vulnerabilities to achieve their goals while minimizing detection.
Although the core functionality remains consistent, Check Point Research has identified changes in tactics, techniques, and procedures (TTPs) that reflect a more cautious target selection and operational security (OPSEC) awareness.
Sharp Dragon’s strategic expansion towards Africa and the Caribbean signifies broader efforts by Chinese cyber entities to increase their presence and influence in these regions. The evolving tactics of Sharp Dragon highlight the dynamic nature of cyber threats, especially towards regions that have been historically overlooked.
